Totally secure internet-browsing in 15 minutes
Browsing the internet without fear
Nowadays, the internet is a hazardous place. There are viruses, trojans, Cookies that store and reveal your data, people phishing your money from your bank account with special worms and so forth. The problem is, you never can be sure if your computer is suffering from malware and re-routes your online-banking-request to some russia servers. Hell, I am not sure myself (and at least I am supposed to know such things).
The old solution: Rebooting your computer
In former times I solved the problem pretty easy: I downloaded a bootable Linux CD, i.e. the Knoppix Live CD. All I had to do was to insert the CD, reboot the computer and, eventually, setup the network so I could browse the internet. The advantage of such Live CDs is obvious: They start a complete and fresh operating system every time, and because they do it from CD, malware can not change the programs or data and install unwanted software on the computer. But, be honest, do you want to reboot your computer (twice, you have to start your original OS again afterwards) to simply transfer some money via online banking? Because this all was to time-consuming I stopped doing it.
The next step was to split responsibilities between different Browsers. "Daily surfing" with IE and "secure surfing" with Firefox. But again, this is not totally safe. I used Firefox more and more and because of that I had to at least empty the caches/cookies/passwords from time to time to regain a little bit of security and privacy. That was no fun, either. And you never know when security holes will be exploited in the future, even if it's Firefox.
The new solution: Virtually, no security holes
Yesterday, I hit on something in the web that sounded promising to solve these problems. It is an article about setting up a virtual machine as a window, just like any other program you use on your computer on a daily basis. The punchline is that you do not have to restart your computer to start an other operating system from a so called Live CD image, no you run the complete OS in a separate window on your desktop. Then you can use Firefox in there to browse the web. And it is easily done, too.
All you have to do is download and install the virtual machine VMWare, get a Live CD - iso-file and setup the VM environment. A so called iso-file is nothing more or less than an image from a CD named "blahblah.iso".
The steps for that (in short form, for more information please visit lifehack.org) :
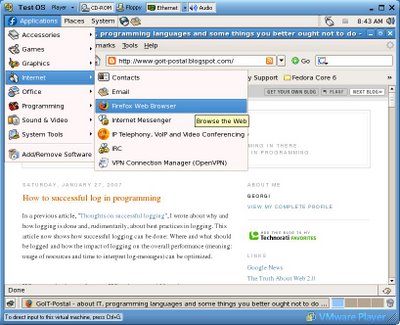 Fedora Core's Firefox is clickable as small icon left from the "System" - menue or in "Applications -> Internet -> Firefox", but this Fedora only serves resolutions up to 800 x 600
Fedora Core's Firefox is clickable as small icon left from the "System" - menue or in "Applications -> Internet -> Firefox", but this Fedora only serves resolutions up to 800 x 600
What happens is that VMWare starts the operating system from the iso-file as if it were an ordinary CD. That bears the advantage that malware cannot install itself on the "operating system in a window". Every time you restart VMWare will be as if you start it the first time. You now are safe to surf whatever you want, after shutting down VMWare your computer is in the same state than before.
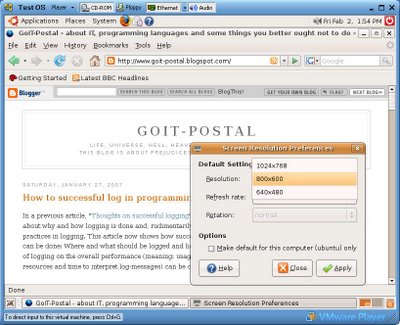 The screen resolution of Ubuntu and Fedora Core can be changed via menue "System -> Preferences -> Screen Resolution", this Ubuntu serves up to 1024 x 768
The screen resolution of Ubuntu and Fedora Core can be changed via menue "System -> Preferences -> Screen Resolution", this Ubuntu serves up to 1024 x 768
Ubuntu and Fedora Core automatically get the network connection from VMWare via DHCP. If you prefer Puppy Linux (because it's smaller, does not use that much resources and therefore starts faster) you will have to run the network wizzard, select the interface by pressing on the button "eth0" and then press the button "Auto DHCP". After this you can browser via the "Browse" - icon left on the desktop.
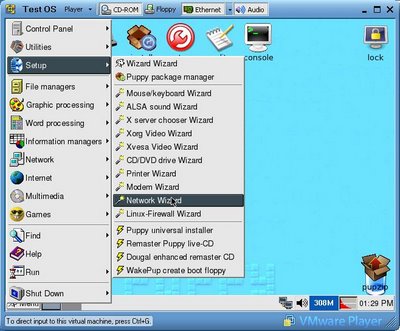 Puppy loves the network: Start the network wizzard to connect. For me Puppy only ran using the Xvesa and not Xorg window system and does not have the Gnome desktop installed.
Puppy loves the network: Start the network wizzard to connect. For me Puppy only ran using the Xvesa and not Xorg window system and does not have the Gnome desktop installed.
Some words on usability and needed resources: I prefer Ubuntu over Fedora Core because it starts faster and provides you with a screen resolution up to 1024 x 768. But this merely is a matter of taste. A Pentium IV with 2GHz (AMD 2500+) and some 512 megabyte of RAM should suffice to run the virtual machine fluently on your computer. You can "suspend" the OS using a VMWare feature, this is like normal going in suspend mode and means that the "operating system window" will be stored on your hard disk. Starting it afterwards keeps your preferences and running programs. But it keeps the cookies, too.
So, happy safe surfing and remember: The fact that you are not paranoid does not mean, that they do not chase after you... .
Nowadays, the internet is a hazardous place. There are viruses, trojans, Cookies that store and reveal your data, people phishing your money from your bank account with special worms and so forth. The problem is, you never can be sure if your computer is suffering from malware and re-routes your online-banking-request to some russia servers. Hell, I am not sure myself (and at least I am supposed to know such things).
The old solution: Rebooting your computer
In former times I solved the problem pretty easy: I downloaded a bootable Linux CD, i.e. the Knoppix Live CD. All I had to do was to insert the CD, reboot the computer and, eventually, setup the network so I could browse the internet. The advantage of such Live CDs is obvious: They start a complete and fresh operating system every time, and because they do it from CD, malware can not change the programs or data and install unwanted software on the computer. But, be honest, do you want to reboot your computer (twice, you have to start your original OS again afterwards) to simply transfer some money via online banking? Because this all was to time-consuming I stopped doing it.
The next step was to split responsibilities between different Browsers. "Daily surfing" with IE and "secure surfing" with Firefox. But again, this is not totally safe. I used Firefox more and more and because of that I had to at least empty the caches/cookies/passwords from time to time to regain a little bit of security and privacy. That was no fun, either. And you never know when security holes will be exploited in the future, even if it's Firefox.
The new solution: Virtually, no security holes
Yesterday, I hit on something in the web that sounded promising to solve these problems. It is an article about setting up a virtual machine as a window, just like any other program you use on your computer on a daily basis. The punchline is that you do not have to restart your computer to start an other operating system from a so called Live CD image, no you run the complete OS in a separate window on your desktop. Then you can use Firefox in there to browse the web. And it is easily done, too.
All you have to do is download and install the virtual machine VMWare, get a Live CD - iso-file and setup the VM environment. A so called iso-file is nothing more or less than an image from a CD named "blahblah.iso".
The steps for that (in short form, for more information please visit lifehack.org) :
- Download and install VMWare for your operating system from this place. You need administrative access to install it, though.
- Download an iso-image of Linux. You can find Fedora Core here (approx. 700mb), Ubuntu Linux here (approx. 715mb) and, the smallest of all, Puppy Linux here. Fedora and Ubuntu will be easy to get up and running and have Firefox in their package, Puppy Linux will need less resources but a little hands-on experience shown below.
- Download the prepared VMWare configuration files from here and unzip them into a new folder. Open the file "OS.vmx" in this folder and edit the line that starts with "ide1:0.fileName =", this option must point to your iso-file. For example, if you downloaded Ubuntu and stored it in "C:\Linux" the line should be - ide1:0.fileName = "C:\Linux\edgy-desktop-i386.iso"
- Doubleclick on the file "OS.vmx" (to start VMWare) and wait.
 Fedora Core's Firefox is clickable as small icon left from the "System" - menue or in "Applications -> Internet -> Firefox", but this Fedora only serves resolutions up to 800 x 600
Fedora Core's Firefox is clickable as small icon left from the "System" - menue or in "Applications -> Internet -> Firefox", but this Fedora only serves resolutions up to 800 x 600What happens is that VMWare starts the operating system from the iso-file as if it were an ordinary CD. That bears the advantage that malware cannot install itself on the "operating system in a window". Every time you restart VMWare will be as if you start it the first time. You now are safe to surf whatever you want, after shutting down VMWare your computer is in the same state than before.
 The screen resolution of Ubuntu and Fedora Core can be changed via menue "System -> Preferences -> Screen Resolution", this Ubuntu serves up to 1024 x 768
The screen resolution of Ubuntu and Fedora Core can be changed via menue "System -> Preferences -> Screen Resolution", this Ubuntu serves up to 1024 x 768Ubuntu and Fedora Core automatically get the network connection from VMWare via DHCP. If you prefer Puppy Linux (because it's smaller, does not use that much resources and therefore starts faster) you will have to run the network wizzard, select the interface by pressing on the button "eth0" and then press the button "Auto DHCP". After this you can browser via the "Browse" - icon left on the desktop.
 Puppy loves the network: Start the network wizzard to connect. For me Puppy only ran using the Xvesa and not Xorg window system and does not have the Gnome desktop installed.
Puppy loves the network: Start the network wizzard to connect. For me Puppy only ran using the Xvesa and not Xorg window system and does not have the Gnome desktop installed.Some words on usability and needed resources: I prefer Ubuntu over Fedora Core because it starts faster and provides you with a screen resolution up to 1024 x 768. But this merely is a matter of taste. A Pentium IV with 2GHz (AMD 2500+) and some 512 megabyte of RAM should suffice to run the virtual machine fluently on your computer. You can "suspend" the OS using a VMWare feature, this is like normal going in suspend mode and means that the "operating system window" will be stored on your hard disk. Starting it afterwards keeps your preferences and running programs. But it keeps the cookies, too.
So, happy safe surfing and remember: The fact that you are not paranoid does not mean, that they do not chase after you... .
Labels: Browser, Internet Explorer, secure
4 Comments:
Georgi, I've written about secure Internet browsing at Secure Internet Banking with a Live CD, and your first solution, with a Live CD, corresponds to what I describe in my article.
The problem you are trying to solve is to protect the environment in which you do sensitive Web surfing, e.g. banking, from your normal surfing environment. Using a Live CD to do the sensitive surfing solves this problem, because the normal environment has no access to the CD, and hopefully the CD-booted system doesn't write any sensitive information to disk. Using different web browsers doesn't solve the problem at all, because each is on the hard disk which is freely accessible by either application. Using VMWare in the way you describe it doesn't solve it, because you are starting your sensitive surfing from within your normal Windows environment. So if Windows is compromised, then VMWare-within-windows can be compromised, and you are not secure any more.
VMWare could perhaps solve the problem, if VMWare was given top-level control, i.e. both the normal surfing environment and the sensitive surfing environment were invoked from VMWare, and if VMWare made sure that each environment only accessed its own disk partition. (I have no direct experience with VMWare, so I am guessing as to its actual capabilities.)
Hello Philip,
thanks for your reply and yes, you are right. Having a VM (virtual machine, like VMWare) running means you are relying on the underlying OS (operating system, like Windows) you started your virtual machine from. But, and that is important, I think in a way you aren't.
Let me try to explain this (and please feel free to correct me in case I'm wrong - security is a process evolving and to be discussed, not to be finalized so you simply can hang around somewhere else :). The advantage of the described procedure is that you load the data for your virtual machine (i.e. OS-kernel, drivers, filesystem etc.) from within a .iso - file that looks and behaves like a CD for the virtual machine. No chance at all from within the loaded OS to be compromised. Unless you compromise the underlying OS which started the VM, or you compromise the VM itself. Well, said that you couldn't be right, eh? No. Time to start the tricky part.
No one is able to guarantee that a VMWare installation runs totally secure if the underlying system is not. Let me state a simple example: The network driver of the hosting OS is infected and always sends requests to one server that - of course - can read all this data before sending it somewhere else (kinda man-in-the-middle-attack). Starting a VM in the hosting OS will merely improve your security because the VM is relying on your origin internet connection, all requests will be send from the VM to your origin OS and then to the fake server. No chance to get better security by running a VM.
Despite of that let us assume that the connection from your network to the internet is a hazardless zone, you do not have any network-drivers infected, your origin OS does not suffer from security holes which belong to "simple" internet connections. And, to be frank, this is the standard case: Virusses and worms nowadays do not work on the connection (or drivers) but on the software on top of it. Like Browsers, E-Mail-programs or the sort. And then the solution to start a browser in a VM is, in my humble opinion, as secure as rebooting from your favourite-state-of-the-art-CD-operating-system. Why?
At first, VMWare is installing it's own network drivers which correspond to your native network drivers and do not need any additional programs (despite of these native drivers). The OS running in VMWare do not see the origin network drivers or infrastructure running on the origin OS that easy. And no chance for the programs you started within the VM to see them anyway.
Secondly, you do not start "your own browser" running on your OS with it's preferences or history. You start it's pendant in the VM, and that does not have the same configuration, cookies or the vulnerability holes compromised through "downloads" or general usage (i.e. through a virus).
Last not leaast, as mentioned before, you start the OS from an iso-image. As long as you do not tell VMWare otherwise, it's the only file system it knows and it treats it like an ordinary CD (you have no write-privileges to it). If you do not tell the so-started OS where to find a writeable filesystem, it simply cannot write down data in any case, if you tell the OS where to store the data, you would have to tell it again, after restarting VMWare. Simple as that.
At least the article was incendiary called "Totally secure internet-browsing ..." - I regret the "Totally secure". Who am I to cry out that safety is totally possible? But the second part is "internet-browsing", and I'm sure that part is true, done right: After restarting the VM no cookies, no history, no worms or virusses (or u-name-it) will be persistent. Having a VM hosting it means that there are no vulnerabilities known (yet). This may change in the future, but: Tricking a VM is far too complex to be used as vulnerability, at least as long as there are other, more simple ways. It's secure because it just doesn't pay off, bet on that.
Greetingsw, Georgi
But how would this technique deal with a keylogger, and how can you asure that the underlying OS isn't compromised if it works with read/write media.
Please forgive my ignorance, I'm trying to learn everything I can about this fascinating issue.
Hello visitor,
to be honest: You cannot guarantee complete security if a system is compromised you rely on (your internet connection / your VM ...). For example: In case a good key logger is installed on your host system then it will (perhaps) log all your keystrokes even if you use a VM to browse.
But the solution mentioned here will greatly improve security and help you: Being (in these examples) a read-only instance means that nobody is able to compromise your system or browser permanently. File exchange can be done by mounting folders from your VM-host and as long as you don't start an executable on your host that will compromise it, you are not in danger to infect your system (the VM will be gone after stopping it anyway).
These iso-images mentioned in the article can be extended by installing software on them, too. But you are able to define the locations where software can write to the file system, so this is not a security issue, too, as long as you do not break security issues: Everything is possible and depends on your ability to administer it correctly. And in case something wents wrong, simply delete the complete system ;-)
Hope this was helpful, greetings, Georgi
Post a Comment
<< Home